Overview
Bizagi can be integrated with a variety of systems that are intended for different purposes. Usually, when a system is integrated with another, an authentication procedure must be executed first, to make sure that the integration occurs only between trusted systems. Due to the variety of systems, and their inherent technologies, access to these systems demand to handle a set of different authentication protocols, for each feature in Bizagi that can be integrated with other systems. For example, when you want to integrate an ECM like SharePoint.
The following picture shows an example where you can have multiple integrations throughout different features available in Bizagi:
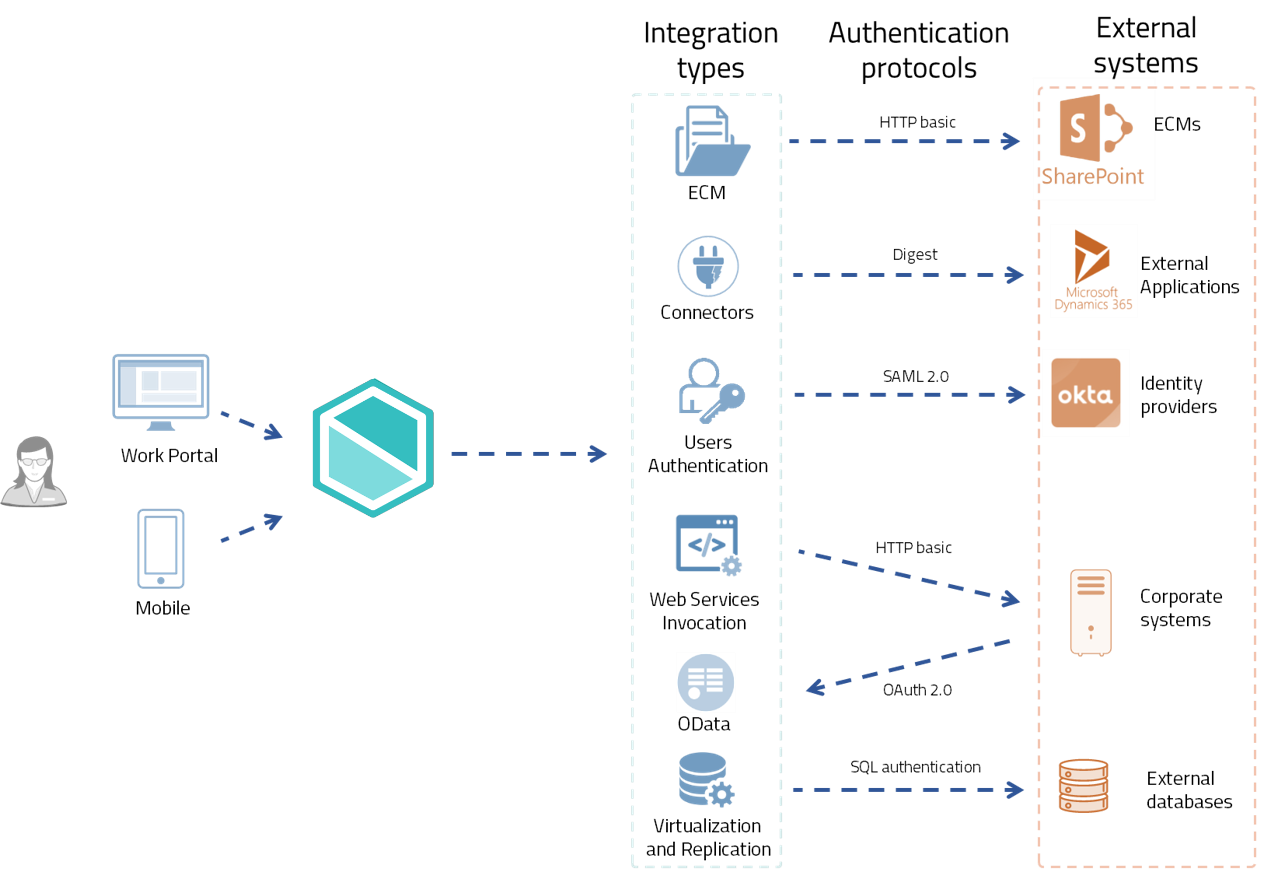
Each feature can use a different authentication protocol. Therefore it is important to understand the protocols available for each feature. The following table sums the different integration types, their available authentication protocols. Here you can find also some of the Identity Providers (IdP) supported. An identity provider is a third-party application that handles the authentication of users.
Click each item to see the authentication protocols.
- Authenticate users in the Work Portal
-
Management Console Web / Customer Portal / AI /BI
Protocol Identity Providers SAML 2.0 Azure AD
ADFS
NetIQ
Okta
PingFederated
Any IdP that supports SAML 2.0WS-Federation 1.0 Azure AD or ASDFS 3.0 or 4.0 Open ID (oAuth 2.0) Okta Multiple Authentication Multiple Id Providers -
ECM
Protocol ECM Providers HTTP basic authentication Sharepoint On-premises, Documentum, Alfresco, FileNet -
Connectors
-
Easy REST connector
Protocol Grant types HTTP basic authentication N/A Oauth 2.0 Client Credential, Password Resource Owner, Impersonation. Digest N/A -
Custom connector
Protocol Grant types Custom authentication Customer creates its own authentication methods
-
Easy REST connector
-
OData
Protocol Token authorization OAuth 2.0 Client Credentials, Bearer token -
Invoke SOAP external web services
Protocol Authorization method Basic HTTP authentication N/A Plan header token N/A WS-Security Secure conversation head token -
Invoke REST external web services
Protocol Authorization method Basic HTTP authentication N/A -
Bizagi SOA Layer
Protocol Authorization method WS-Security Basic user profile - Virtualization and Replication (requires VPN)
- Apps
- Mobile
Additional to authentication protocols set for integrations and features, there are other aspects of security that you can configure. You may define the following security aspects in a project:
Work Portal Security
Bizagi allows you to restrict access to different areas of your processes during execution to make sure that the correct people have the necessary privileges and prevent unauthorized actions.
Bizagi offers the Security Module that allows you to define a schema of permissions on some of the elements, which includes:
•How are users authenticated.
•What options can each user see or use (according to roles, positions, location, etc).
•Which processes and tasks are available for mobile device access.
For more information refer to Work Portal Security.
Case security
Bizagi allows you to include additional security measures for the management of information that is a very sensitive, in order to comply with your data confidentiality policies.
In scenarios in which special controls are required to limit the data exposure for the different actors and roles using Bizagi Work portal, you may indicate which users have permissions over specific business information (at cases level).
For more information refer to Case security.
Last Updated 1/16/2026 2:15:51 PM