Overview
With Automation Service or Studio Cloud Services, you can integrate your business processes with any system or application offering a public endpoint.
If your systems or applications do not offer a public endpoint, you can establish a VPN to allow access to them while ensuring that data is encrypted in transit.
About the VPN
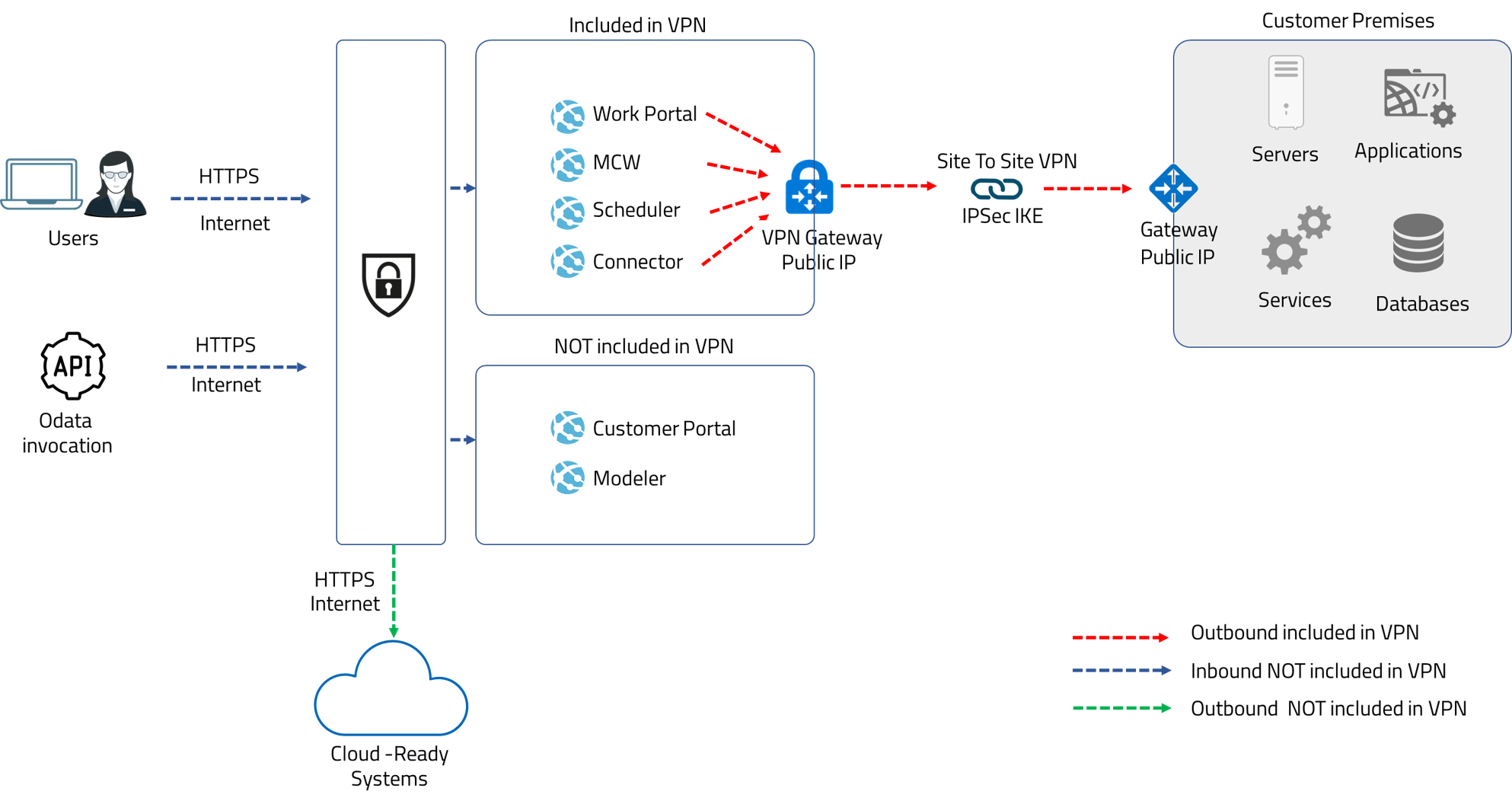
The VPN is intended for integration purposes. When processes need to reach systems, servers, services, or databases that are not exposed via the internet, the VPN is a secure way to access those systems.
You can use VPN for application integration, whenever your processes in Automation Service connect to any of these:
•A web service (SOAP, RESTful) which is set up inside of network and does not offer a public endpoint.
•An Active Directory server (e.g, for use of LDAP authentication in Bizagi or the LDAP users synchronization module).
•A SQL Server database which is set up inside your network and does not offer a public endpoint.
•An SMTP server which is set up inside your network and does not offer a public endpoint.
•Other corporate services, ESBs, or assets, which are set up inside your network and do not offer public endpoints.
Note: Consider that when integrating an external application or service whose access is routed through the Internet or a VPN, a certificate issued by a public CA is required for your server. Self-signed certificates or local CA’s are not supported. If the web service has a self-signed certificate or one from an internal CA, Bizagi will not be able to validate the site, resulting in an SSL error. This means the handling of certificates will be the same as if the integration were done via the internet with a public endpoint.
The only exception is when using connectors for integrations, where certificates can be embedded directly within the code allowing the use of self-signed or custom certificates in that specific context.
|
•Access to all Bizagi portals, including Customer Portal, Modeler Services, Management Console, and any other related portals, is not provided through the VPN. •Because the VPN is intended for integration purposes, it should NOT be considered as an additional security measure to restrict access to your automation environments. •White List: If needed, you can request, through a support ticket, to enable an IP address White List. So only IP addresses in the list can access any of your Bizagi cloud-based portals. |
Example
Implementation of Certificate for webserver01.contoso.loc
In a corporate network environment, the fictional company "Contoso" has deployed a server named "webserver01" with the network domain "contoso.loc". They want to integrate the services of this server with Bizagi. To achieve this goal, it has been decided to implement and maintain an SSL/TLS certificate for the server, with the exact domain name "webserver01.contoso.loc".
|
The handling of certificates will always be the same as if the integration were done via the internet with a public endpoint, even if a VPN is being used. |
Network Environment
•Server Name: webserver01
•Network Domain: contoso.loc
•Operating System: Windows Server
Implementation of SSL/TLS certificate
•A SSL/TLS certificate is acquired from a trusted certification authority.
•The certificate must be issued for the specific hostname "webserver01.contoso.loc", ensuring that connections are only established with this server and not with potential fraudulent servers.
•The certificate is installed and configured on the webserver01 server to ensure that inbound and outbound connections are protected.
Certificate Renewal
•Since SSL/TLS certificates have an expiration date, it is necessary to establish a process for periodic renewal to ensure security continuity.
•A reminder and an automated procedure are set up to renew the certificate before it expires, preventing service interruptions due to an expired certificate.
In summary, the continuous implementation and renewal of the SSL/TLS certificate for "webserver01.contoso.loc" are crucial to ensure the security and integrity of communications in the Contoso network environment. This helps protect sensitive data and maintain the trust of both internal users and external clients in the services provided by the webserver01 server.
Configuration
The first step to establishing a VPN is to contact your Bizagi sales representative to purchase the service.
Additionally, configuring a VPN requires support from your IT and Security teams. You'll need an expert to assist with configuring, monitoring, and managing VPN-related aspects that depend on your organization's specific setup.
To use a VPN, certain technical requirements must be met.
You 'll need a supported VPN device, either on-premises or in the cloud, with a Public IP Version 4 (IPv4) assigned to it.
The device must also be capable of being configured with the IPsec protocol.
You’ll be required to provide specific details to receive tailored instructions for the next steps on your end.
Bizagi supports the VPN configurations based on Azure, its IaaS platform. Therefore, the VPN devices that are supported are those listed at https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpn-devices. Ensure that the VPN device your organization plans to use is listed as supported.
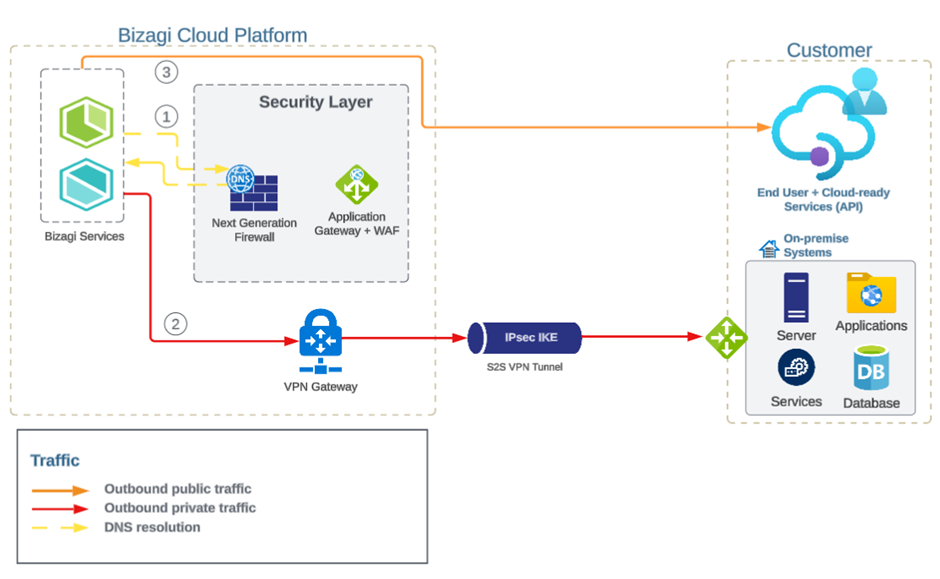
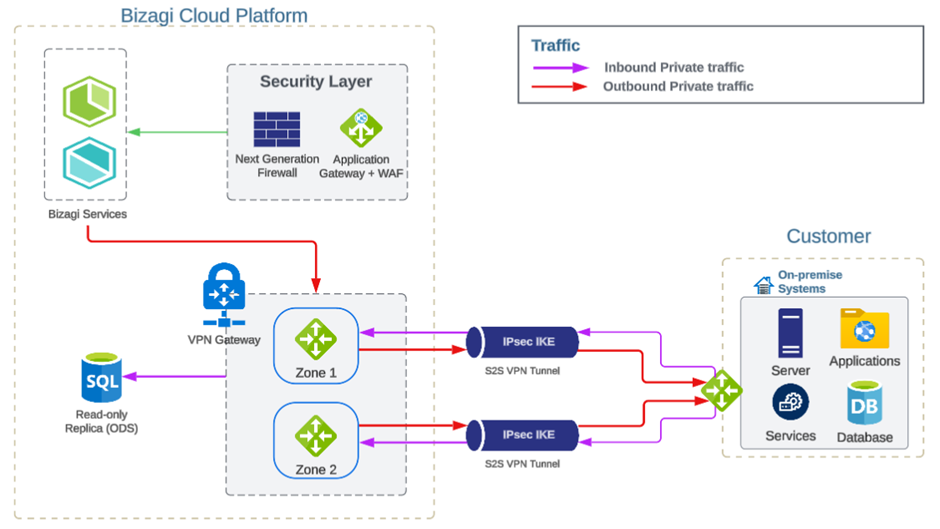
Outbound traffic
Outbound traffic will be routed to the VPN according to the definitions in the encryption domains. If it’s necessary to enable to access a private resource through a VPN using a custom Fully Qualified Domain Name (FQDN), there are a few important steps to follow:
1.Encryption Domains: The site you're trying to access must be included in the correct encryption domain. This defines which networks or systems should be encrypted when communicated through the VPN.
2.Security Policies: Ensure that the appropriate security policies are in place. These policies control who can access what resources over the VPN and under what conditions.
3.Private DNS Record: Submit a support ticket providing the necessary DNS records that should be created (1). This allows the system to resolve (or translate) the domain name into the correct IP address to access the private resource.
Note: Any traffic not included in the encryption domain or associated with an undefined private DNS record will be sent over the internet.
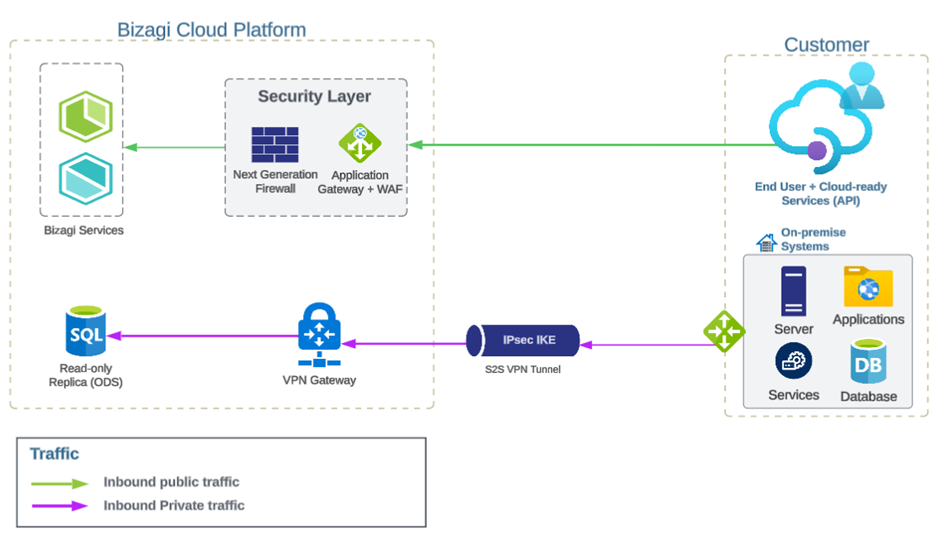
Inbound traffic
Inbound traffic to Bizagi Cloud environments is routed via the internet, which is the recommended approach for its simplicity, performance, and ease of management. This configuration allows efficient access to devices and services for users and customers, while ensuring that the only inbound traffic permitted is for accessing the ODS server.
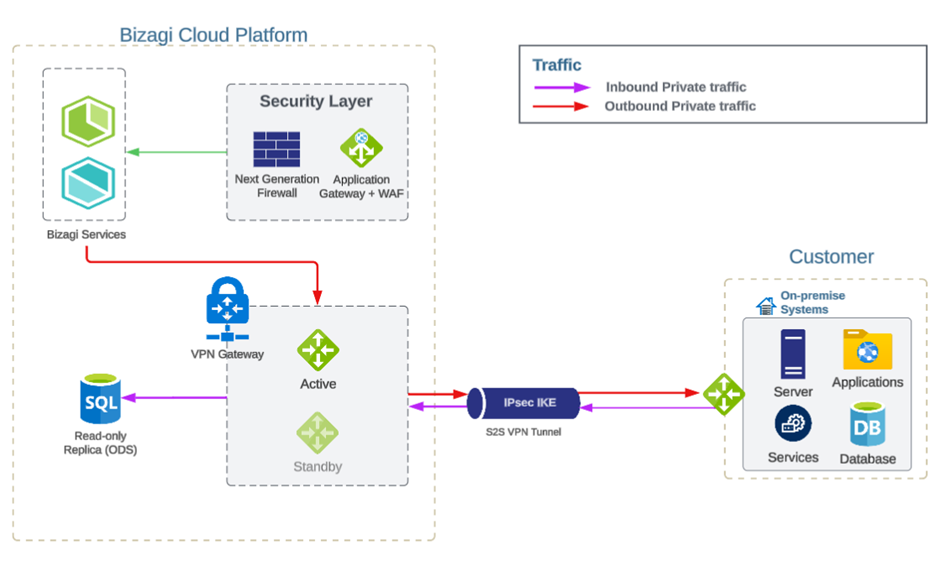
Redundancy
Every VPN established is configured with two instances in an active-standby setup, ensuring that if the event of any planned maintenance or unexpected disruption affecting the active instance, the standby instance will automatically take over and resume the Site-to-Site (S2S) connections.
While the switch-over may cause a brief interruption, connectivity is typically restored within 10 to 15 seconds during planned maintenance. In the case of unplanned disruptions, the recovery time may extend to 1 to 3 minutes, depending on the severity of the issue.
Enhanced availability
For customers consuming more than 500 BPUs per month, or those who have purchased Enhanced Availability for a Service Level Agreement (SLA) for the Production environment of 99.99%.:
The Production environment is configured with a VPN established across two active-active instances, deployed in a zone-redundant setup. This configuration enhances resilience against unplanned disruptions by leveraging independent power, cooling, and networking infrastructure. In the event of an outage in one zone, regional services and capacity remain available.
FAQs
Consider the answers to these typical questions:
1.What is a VPN?
A virtual private network (VPN) is a technology that extends a private network across a public network, providing a tunnel over the communication channel while encrypting transmitted data. In this specific case, it means securely extending your corporate network to Automation Service, over the internet.
Transmitted data refers to the data exchanged between Automation Service and your corporate network for application integration requirements.
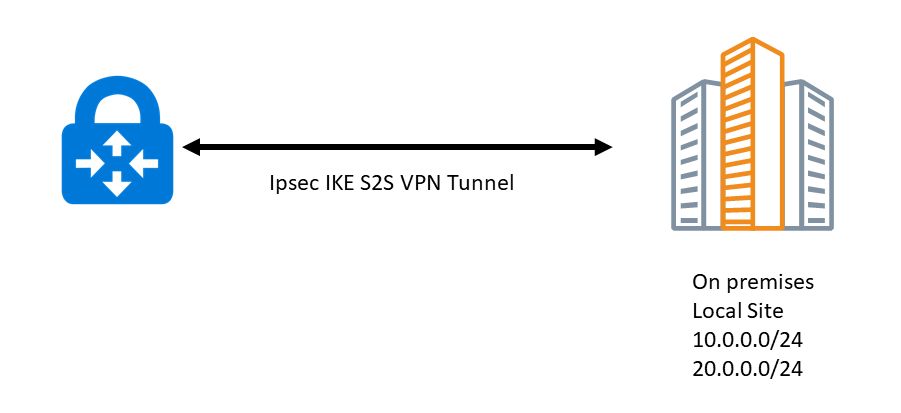
2.What is a VPN tunnel?
While a VPN is a network, the pathways used by data to pass through in such network are known as tunnels. Tunnels are created through different types of tunneling protocols. Settings such as speed and encryption complexity vary depending on the protocol.
These tunnels are encrypted connections, and you may have several of these tunnels inside a VPN.
Consider the number of connections for a VPN, since these tunnels are limited, as well as the bandwidth offered for the VPN. There are different types of connections. A site-to-site connections (as the one we use) uses a connection over IPsec/IKE (IKEv2) VPN tunnel.
3.How long will it take to configure a VPN
How long it takes to set up a VPN depends mostly on your IT administration and governance procedures. A VPN requires that certain configurations are carried out at each of the two endpoints (one of these being under the control of you and your IT team). Configuration of the VPN's endpoint directly in Automation Service will not take more than one business day, provided that you provide the details we need for the configuration.
4.Does the use of a VPN provide additional security to end users?
Access is routed through the public internet via HTTPS, which already takes charge of encrypting data in transit. Inbound connections pass through the security layer, which is a robust security measurement for your Automation environments. However, the VPN is not intended to restrict access to your environments. You can request a white list configuration, so IP addresses can be included in the list as the only ones permitted to access any of the Bizagi cloud-based portals and give additional security.
5.Does the use of a VPN allow me to target Automation Service or Studio Cloud Services (or any of its underlying assets) from an on-premises system?
No, similarly to the above question, a VPN allows Automation Service or SCS to target your on-premises systems.
6.What algorithms support VPN?
IKE Version: Only 2
Gateway VPN type: Route-based gateway
Phase 1:
•IKEv2 encryption: GCMAES256, GCMAES128, AES256, AES192, AES128
•IKEv2 integrity: SHA384, SHA256, SHA1, MD5
•DH Group = 1, 2, 14, 19, 20, 24, None
Phase 2:
•IPSec encryption: GCMAES256, GCMAES192, GCMAES128, AES256, AES192, AES128, DES3, DES, None
•IPSec integrity: GCMAES256, GCMAES192, GCMAES128, SHA256, SHA1, MD5
•PFS Group = 1, 2, 14, 19, 20, 24, None
7.Can I use a fully qualified domain name (FQDN) to establish the VPN?
Yes, it is possible to establish a VPN connection using a Fully Qualified Domain Name (FQDN). However, the FQDN must resolve to an IPv4 address. If the domain name resolves multiple IP addresses, the VPN will use the first IP address returned by the DNS server.
Additionally, it's important to note that the VPN maintains a DNS cache, which is refreshed every 5 minutes. The gateway will attempt to resolve the FQDN only for disconnected tunnels. Resetting the gateway also triggers the resolution of the FQDN.
8.Does the use of a VPN entail an additional cost?
No, Bizagi Bundles include a VPN that you can choose to enable if required by your automation needs.
9.Can multiple Site-to-Site tunnels be created?
Yes, it is possible to create up to 10 stable Site-to-Site tunnels. However, it is very important to ensure that each tunnel is configured clearly and correctly to avoid any issues with overlapping or network routing.
10.Which aspects should I look after when using a VPN?
In case that your IT department needs to perform any change in your infrastructure and servers location, network, VPN device or one that affects an operational VPN, please notify us directly at cloud@bizagi.com.
11.What is the VPN support and SLA?
The SLA offered for the VPN is 99.9% of availability. The SLA and uptime excludes downtime resulting directly or indirectly from any issue arising at your network's VPN endpoint, or from any changes done by you at your network's VPN endpoint without previous notice.
12.If I use a VPN, do I get a dedicated channel for my data to travel through the network?
No, even if you purchase a VPN or not, all the data is sent through public HTTPS.
Last Updated 1/8/2026 9:12:22 AM