Overview
Local certificate support enables invoking web services with local or self-signed certificates, whether called from a rule, the component library, or system interfaces.
This feature is relevant only when using a VPN, to enforce secure TLS traffic with your integrated servers/services (e.g., HTTPS web services, SMTPS emailing, FTPS file transfers, etc.).
In Windows environments, this functionality ensures seamless integration and certificate validation through tools like Microsoft Management Console (MMC) or PowerShell, enabling secure interactions with web services even when using non-commercial or self-signed certificates. Similarly, in OpenSSL, administrators can manage and verify certificates, generating fingerprints as unique identifiers for secure communication across platforms. This capability enhances flexibility and security, supporting robust service integration within diverse IT infrastructures.
To enable this feature, you need to configure a Custom parameter in the Management Console as described below.
What you need to do
To enable local certificate support, add the Custom parameter AllowedLocalCertificatesWhitelist in the Environment settings of the Management Console. Follow these steps:
1.Under the Environment tab, click Options.
2.Click the Custom tab.
3.Click Add Property.
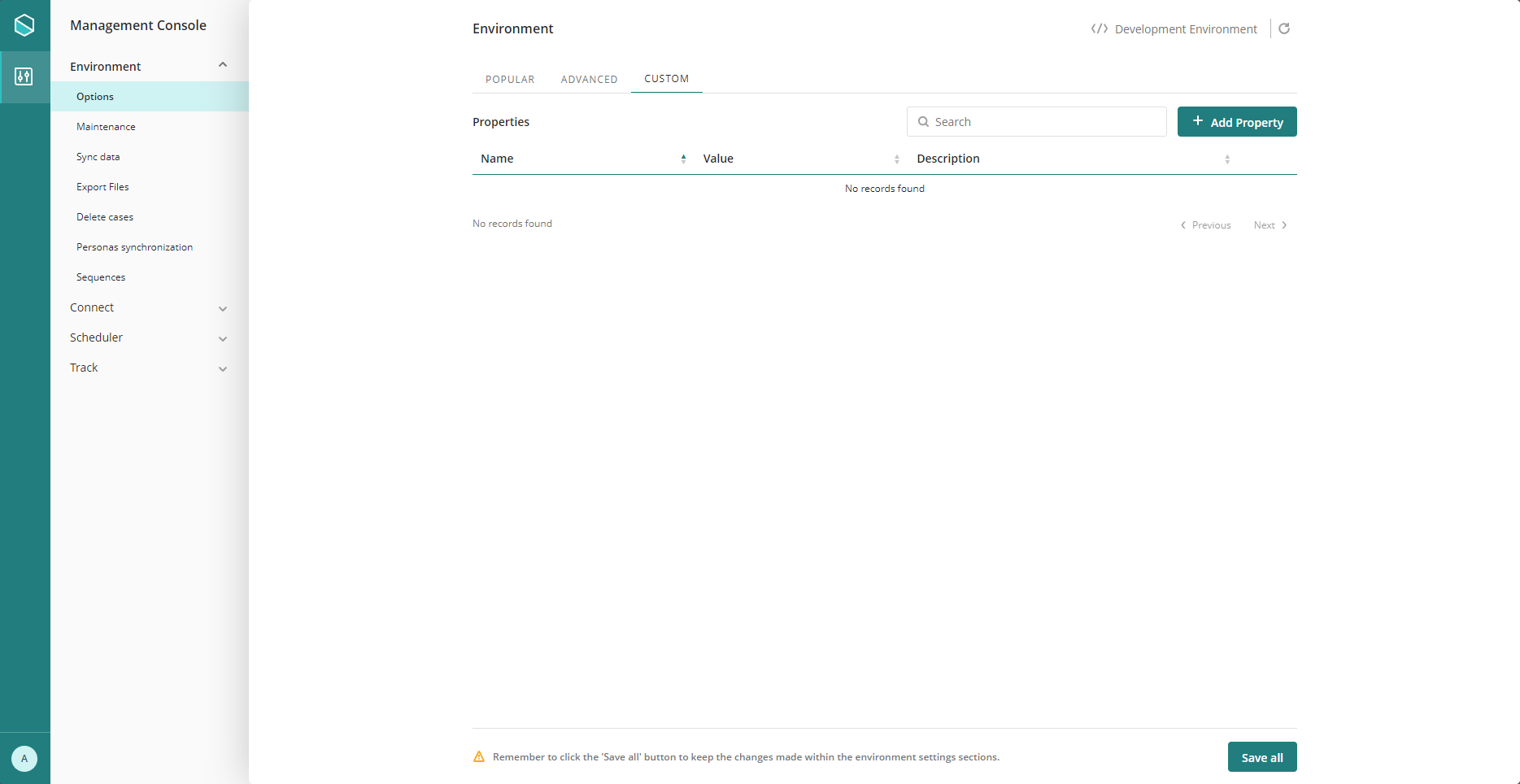
4.In the Add Property window, enter the following values:
•Name: AllowedLocalCertificatesWhitelist
•Value: Your certificates' thumbprints separated by commas. Refer to How to extract the Thumbprint of a certificate for details.
|
The list applies only to self-signed certificates. If a self-signed certificate is used, the system will check whether its thumbprint is included; if it is not, the connection will be denied. Trusted certificates are not affected by this setting and will be validated regardless of whether they appear in the list. |
•Description: A brief description of this property.
5.Click Add to save the property.
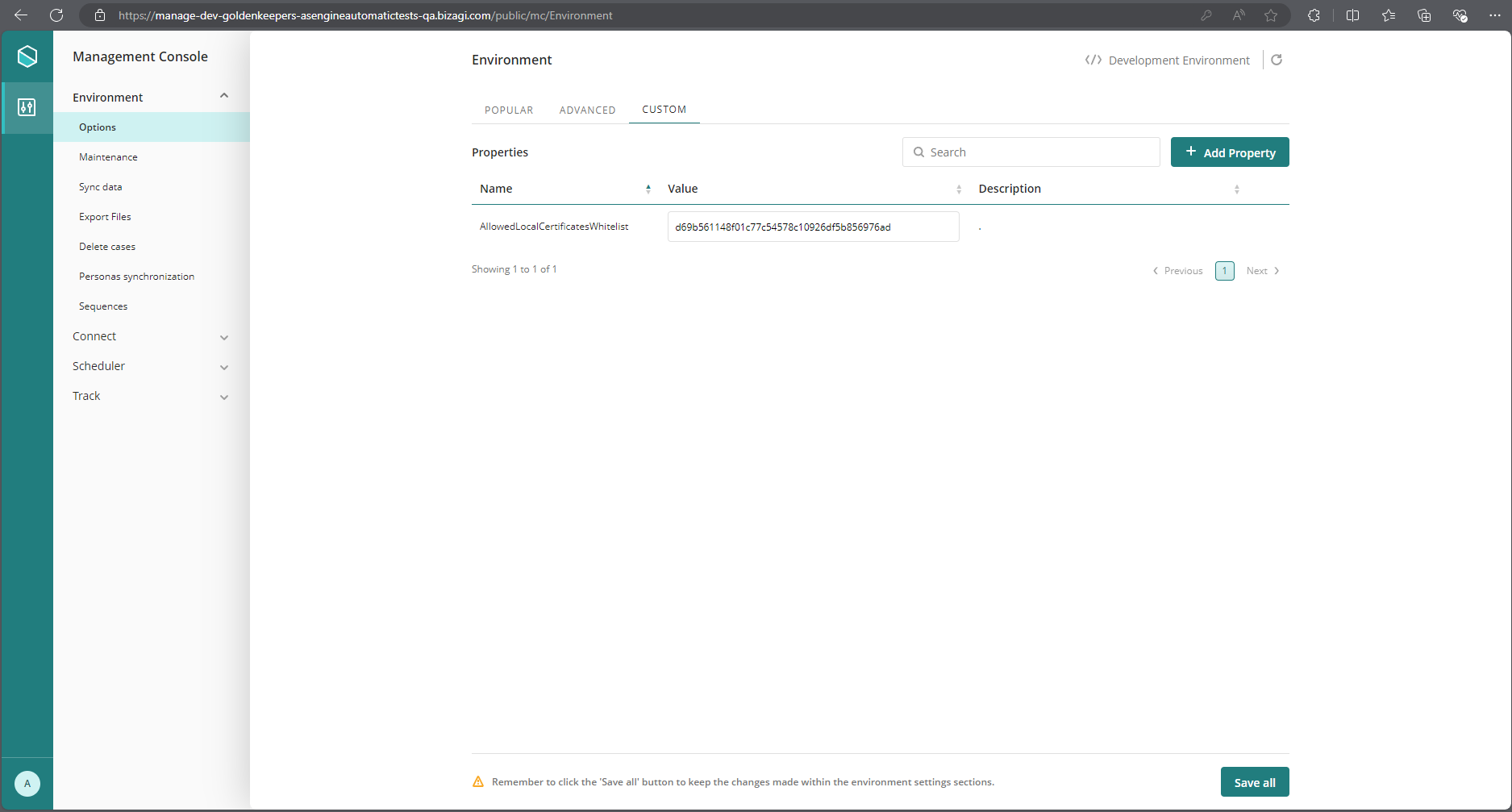
|
After configuring or updating the AllowedLocalCertificatesWhitelist parameter, a full restart of the environment's services (including the Work Portal, Scheduler and Connectors) is required to ensure that certificate changes take effect. |
Last Updated 8/11/2025 6:17:16 PM