Overview
Whenever you need a external application to invoke Bizagi using the features of different services (OData, Azure Active Directory, System for Cross-domain Identity Management, etc.), you must first register the OAuth keys (clientSecret and clientID) used for its authentication in the OAuth 2 Applications option of the Work Portal's Admin menu.
As these services in Bizagi are protected and rely on the OAuth 2.0 standard authentication mechanism, requests made to these services need to be granted rights to resources using the previously generated OAuth keys.
With the OAuth 2.0 specification, Bizagi supports several OAuth flows, which are the most commonly used ones:
•Authorization code: Lets client applications authenticate users with inputted credentials at runtime (through a login page). This flow is designed for human interaction, where requests use impersonation of end users. For more information about this specification, refer to RFC 6749, section 1.3.1.
•Client certificate: Allows applications to authenticate using a digital certificate instead of traditional tokens. This enhances security when consuming OData services, as the application sends a signed JSON Web Token (JWT) validated against the certificate uploaded in Bizagi.
•Client credentials: Allows server-to-server integration without requiring end-user credentials. For more information about this specification, refer to RFC 6749, section 1.3.4.
•Bearer Token: Lets client applications authenticate using a token. For more information about this specification, refer to RFC 6750.
Register Application options
To register an external application, you must first go to the Work Portal and, under the Security section of the Admin menu, select the OAuth2 Applications option.
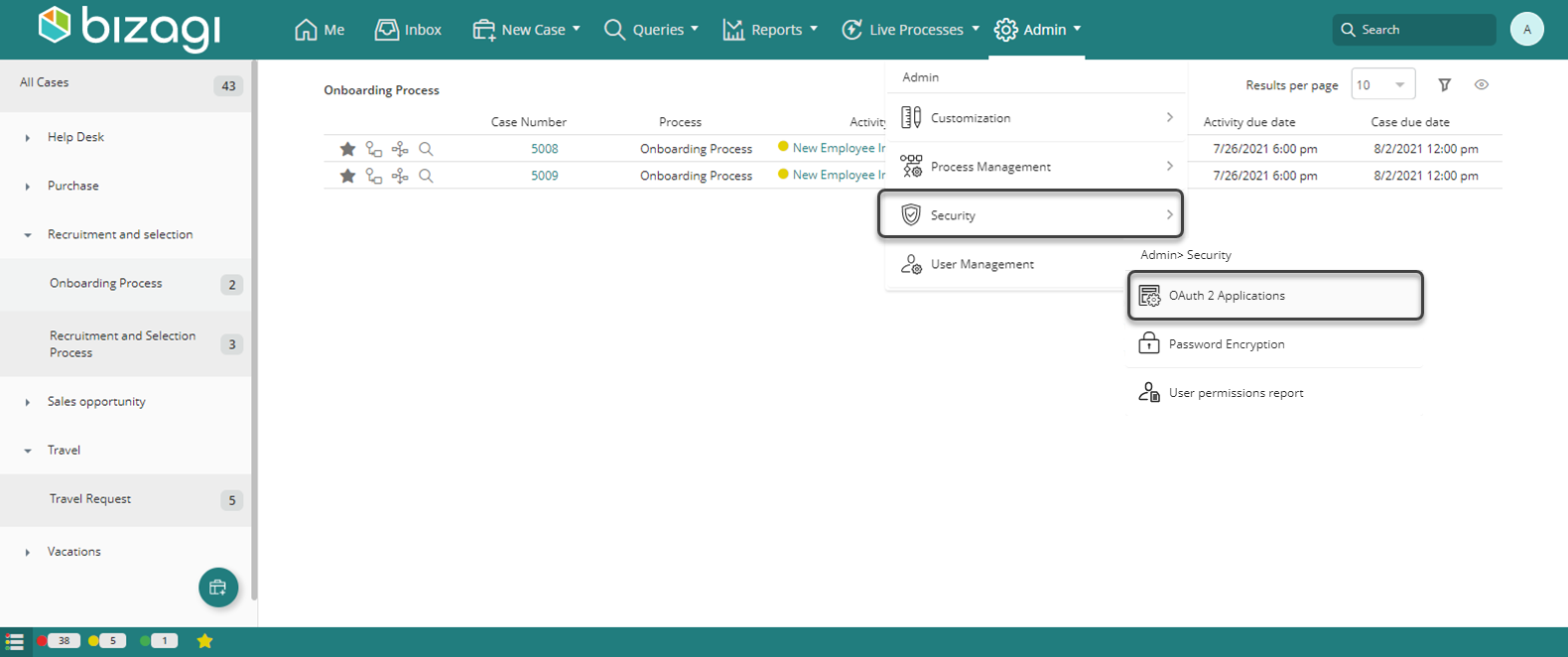
This option lists the services accessed by Bizagi devices and allows you to include additional applications that represent granted access to these services by providing the appropriate access keys.
Click the Add option to create a new record in this table:
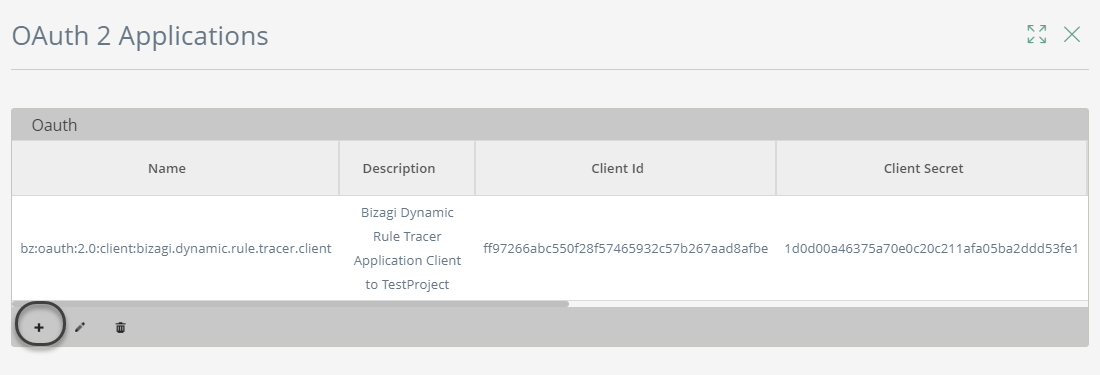
This opens the Register Application window, where you have the following options:
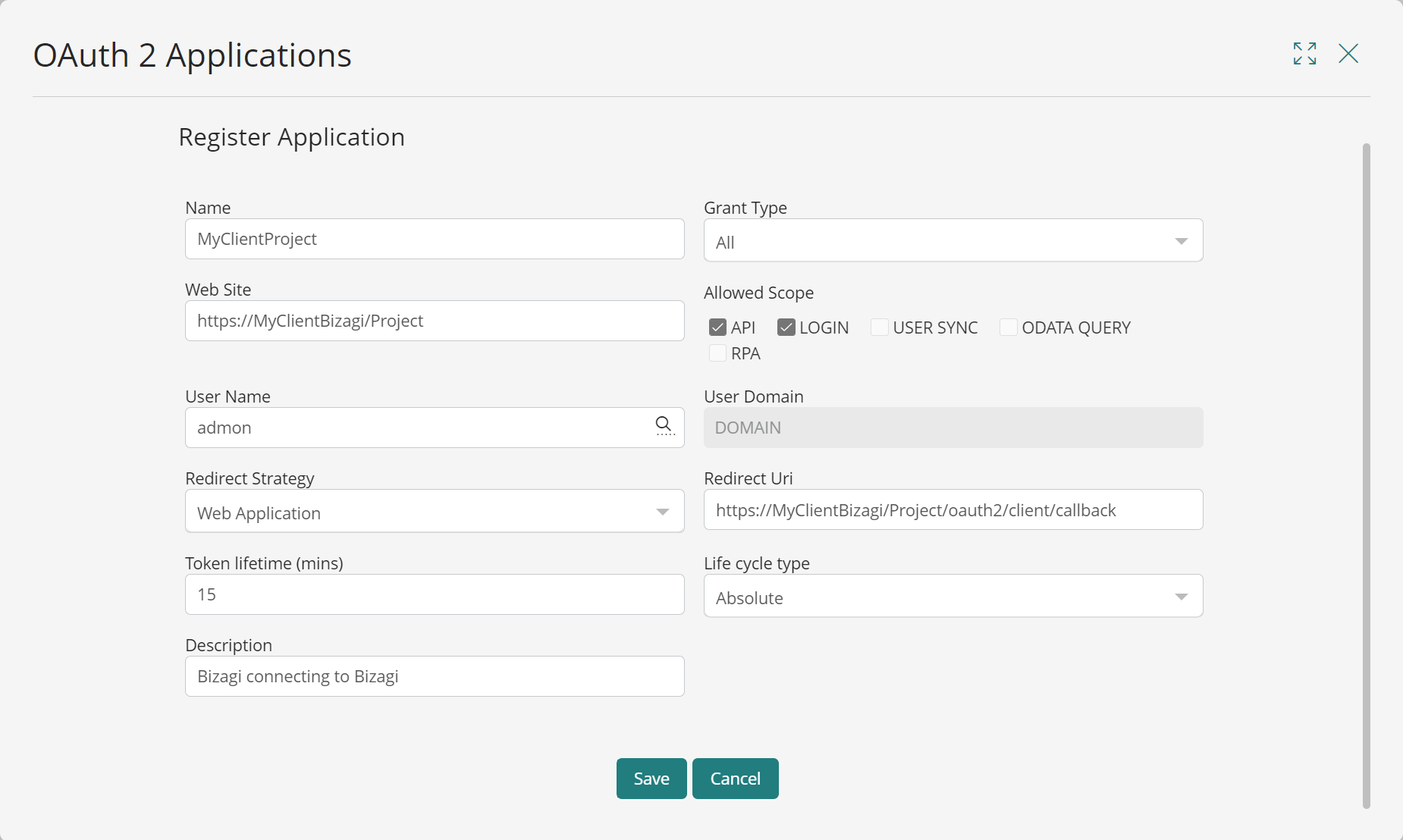
Option |
Description |
|
|---|---|---|
Name |
A unique and representative name that identifies the application being registered. |
|
Grant type |
Authorization Code |
Used to integrate web or mobile applications in which the application receives an authorization code via the redirect URL. Before obtaining the token, the authorization code is sent to the authorization server to reduce the possibility of attackers obtaining the token directly. |
Client certificate |
Allows authentication using a certificate. When this option is selected, the Allowed Scope is automatically set to ODATA QUERY, which is the only available scope for this grant type. This method enhances security for consuming OData services, as the application sends a signed JWT validated against the certificate uploaded in Bizagi. |
|
Client credentials |
Used to obtain an access token in the context of a user (for example, to obtain an access token as an administrator). This option is commonly used when you need to use a Bizagi feature without considering all application users (for example, when using the OData layer as the admon user). With this grant type, there is no need to send an authorization code, as the OAuth keys are validated directly to obtain the access token. |
|
All |
Used to obtain a token via an Authorization Code, Client credentials, or a Bearer token. |
|
Bearer token |
Used as an HTTP authentication scheme, allowing an external application using the OAuth key pair to obtain an access token directly by sending these keys in the authorization header of the HTTP request (for example, when synchronizing users using SCIM). This grant type is recommended when using an HTTPS secure connection. |
|
Web site |
Associated website URL. |
|
Allowed Scope |
API |
When selected, the token allows full use of the OData services. |
LOGIN |
When selected, the token allows the Bizagi project to act as an IdP (authenticator) to access other Bizagi projects. This scope is especially recommended when using Authorization Code as the grant type. |
|
USER SYNC |
When selected, Bizagi uses the SCIM standard to retrieve user information from an external system. You must select this scope when synchronizing users through SCIM. |
|
ODATA QUERY |
When selected, the token grants specific permission to execute Work Portal queries using the Query endpoint of the OData services. This is the only available scope for applications using Client certificate as the grant type. |
|
RPA |
When selected, the token grants permission to respond to Automation Anywhere Callbacks. |
|
User Name |
Applies when using Client credentials, Client certificate, or All as the grant type.
Specify the name of an existing Bizagi user (make sure to select it from the suggested list of matching users).
Security recommendation: When selecting the user name associated with the OAuth 2.0 application, avoid using the default administrator account. Assign a user with the minimum privileges required to perform the intended integration tasks. Granting elevated roles (such as administrators) increases the risk of data exposure through the OData API if the client credentials (clientID and clientSecret) are compromised.
Bizagi does not enforce default role restrictions, so it is your responsibility to define and assign appropriate roles. We also recommended to rotate the clientSecret periodically to reduce the risk of credential misuse. |
|
User Domain |
The domain to which the previously selected user belongs. |
|
Redirect Strategy |
Web Application |
Redirects the user to a web URI using the code obtained from the authorization server. |
Mobile Title Bar Browser |
Used when the application redirects the user to a mobile device app. Since mobile devices do not have an endpoint, the request is redirected by sending the authorization code in the HTML title tag, so the mobile device can extract it from there. |
|
Mobile Localhost Port |
Bizagi sends a code to https://localhost:port/, where a mobile device can retrieve the one sent by the authorization server. |
|
Redirect URI |
Applies when using Authorization Code or All as the grant type.
URL to which the user is redirected in the callback after providing their credentials. The URL should always be defined using HTTPS. |
|
Token lifetime (mins) |
The number of minutes a token remains valid and can be reused for another invocation. This limit enhances security while avoiding replay attacks. If no value is specified, Bizagi considers the token to never expire (infinite lifetime). |
|
Life cycle type |
Absolute |
Token life cycle type in which the authentication session expires once the token lifetime ends, regardless of whether the external system was used or not. When a timeout occurs, a new token must be negotiated. |
Sliding |
Token life cycle type in which the authentication session expires once the token lifetime ends, but unlike the absolute type, the session time resets each time the external system is used. |
|
Description |
A brief description of the registration. |
|
Public key (.cer) |
Applies only to the Client Certificate grant type.
Upload the public certificate file provided by your IT team or system administrator. |
|
Once you have finished selecting and completing the required options, click the Save button.
The OAuth keys (clientID and clientSecret) are generated for authentication of the external system you just registered. Save these keys in a secure location and use them to grant access to the external application.
Last Updated 11/18/2025 11:51:59 PM